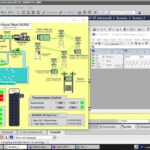
An industrial IoT (IIoT) platform is the software layer that connects machines, collects data from sensors and control systems, and turns that data into actions like alerts, work orders, dashboards, and model-driven insights. Think of it as a translator and traffic cop for your plant data. It gathers signals from PLCs, meters, drives, and gateways, then routes clean, trusted information to the people and systems that need it.
These platforms aren’t used by one team. Operations wants visibility (OEE, line stops, bottlenecks). Maintenance wants early warning (vibration, temperature, runtime patterns). Engineering wants data to improve processes. IT wants secure access, governance, and cost control. In energy and utilities, teams care about reliability and audit trails. In logistics, they care about uptime, asset tracking, and remote monitoring across sites.
This guide is about comparing industrial iot platform vendors without getting pulled into sales decks. You’ll learn what “good” looks like in 2026, the tradeoffs that matter after the pilot, and a simple shortlist process you can run with both OT and IT in the room.
What to expect from an industrial IoT platform in 2026
Most industrial IoT platform vendors claim the same outcomes: fewer surprises, better uptime, lower energy use, faster troubleshooting. The difference is how they get there, and how much work you’ll own during rollout.
At a minimum, you should expect these table stakes:
- Industrial connectivity (common protocols, reliable ingestion, clear diagnostics)
- Time-series data handling (storage, querying, retention controls)
- Basic visualization (dashboards, trends, simple KPIs)
- Rules and notifications (alerts that don’t flood your teams)
- User and access controls (roles, audit trail, SSO options)
- APIs and integration paths (so data doesn’t get trapped)
Newer expectations in 2026 are less flashy but more important: strong edge support for unstable networks, “AI-ready” data that’s labeled and consistent, and security designed in from day one (not bolted on during procurement). If a vendor can’t explain how they handle messy plant data, they’re not ready for a real factory.
Core capabilities you should get out of the box
First, you need device onboarding that doesn’t feel like a science project. That includes templates, bulk import, and clear status so techs can see what’s connected and what’s failing.
Next is data ingestion. The platform should accept both high-rate signals (like vibration) and slower tags (like energy meters) without confusing timestamps or dropping messages.
Protocol support matters because it affects how much middleware you’ll need. OPC UA and MQTT are common starting points; OPC UA is often tied to industrial semantics and secure sessions, while MQTT is a lightweight publish-subscribe pipe. If your team is still bridging older interfaces, it helps to understand the differences and see the OPC DA vs OPC UA comparison.

You’ll also want time-series storage with retention policies, plus dashboards for trends and KPIs that don’t require a full-time developer. Add rules and alerts for conditions like “motor current spikes for 10 seconds” and basic user roles so maintenance, ops, and contractors don’t share one login.
Edge and connectivity options that reduce downtime risk
Cloud-only looks clean on a whiteboard. Plants are messier. Networks go down, switches get replaced, VLANs change, and some equipment must stay isolated. That’s why edge matters.
Look for gateways and edge agents that can run near the machines. Key functions include offline buffering and store-and-forward, so data keeps collecting during outages and syncs later without gaps. This reduces false alarms and keeps your history intact for investigations.
Edge processing is needed when you have low-latency needs (fast interlocks, short-cycle lines), limited bandwidth (remote pumping stations), data privacy constraints, or unreliable connectivity (yards, ports, mines). It can also reduce cloud costs by filtering and aggregating data before sending it upstream.
Ask how the vendor handles remote updates. If you can’t patch edge components safely, you’ll end up with a fleet of mismatched versions. For a concrete example of what an industrial edge gateway is expected to do, see this edge computing solution PAS900 overview and compare it to the edge model your vendor proposes.
How to compare industrial IoT platform vendors without getting lost
The fastest way to waste time is to compare vendors based on who has the longest feature list. A better approach is to anchor on your use cases, then test integration reality, then validate security and support. The winner is usually the platform that fits your plant, your team, and your timeline, not the one with the most charts.
Treat evaluation like buying a work truck, not a sports car. You care about reliability, maintenance, parts availability, and whether it fits your routes.
A practical framework is:
- Confirm the platform can support your top use cases with your data rates and workflows.
- Validate integrations with the systems you already run (PLC, SCADA, historian, MES, ERP).
- Review security and support with IT and OT together.
- Run a short proof of value using real equipment data, then decide.
The proof of value should be small but real. If a vendor can’t connect to your tags in days, rollout won’t get easier later.
Start with your top use cases, not a feature checklist
Use cases force clarity. Here are common IIoT goals and what they demand from the platform:
- Condition monitoring: steady ingestion, clean time stamps, trend views that technicians trust.
- Predictive maintenance: long history, labeled events (failures, repairs), model training and feedback loops.
- OEE and downtime tracking: fast state changes, reason codes, alignment with production schedules.
- Energy monitoring: meter integration, aggregation (shift, day, product), cost allocation by area or line.
- Quality traceability: lot and batch context, links between process tags and test results.
- Remote monitoring: multi-site management, role-based access, alarms that route to on-call staff.
- Digital work instructions: workflow steps, audit trails, and hooks into maintenance systems.
A simple test is to ask: when an alert fires, what happens next? If the answer is “someone checks a dashboard,” you’re missing workflow. Many teams tie platform events back to PLC and maintenance practices; this quick primer on PLC programming in IoT applications can help align expectations between controls and software teams.
Check real-world integration; it’s where most projects slow down
Integration is where pilots become year-long projects. Your platform needs clean connections to PLCs and SCADA, plus a plan for historians, MES, and ERP if you want business context.
Ask vendors to show, in plain language, how they handle:
- Historian integration: can you read existing history and avoid duplicate storage?
- APIs: are they well-documented, versioned, and stable?
- Pre-built connectors: useful, but check limits and licensing.
- Data modeling: can you map tags into assets, lines, and sites without rewriting everything?
- Identity integration (SSO): does it fit how your company manages accounts?
Also ask about “messy reality.” Plants often have tag names like AI_1034 and units that don’t match. A vendor should explain how they normalize names, convert units, and track metadata so “psi” doesn’t get mixed with “bar.” If your environment includes Siemens engineering workflows, it’s fair to ask how the platform aligns with tooling and versioning practices, and what security changes can affect OT engineering, see TIA Portal V20 Update 4 features.
Security, compliance, and support are the deal-breakers
A platform that looks great but can’t pass a security review won’t ship. You want identity and access management with least privilege, plus strong authentication options. Ask how the vendor handles encryption in transit and at rest, key management, and audit logs.
Industrial environments add constraints: segmented networks, jump hosts, strict firewall rules, and limited outbound access. Vendors should be comfortable with OT patterns, not surprised by them.
For compliance, many buyers request third-party reports like SOC 2 and certifications like ISO 27001, and they may ask how a vendor aligns with IEC 62443 concepts for industrial security. You don’t need to be a standards expert, but you should ask for evidence and scope, and confirm what parts of the service the report covers.
Support is just as important. Clarify the support model (ticketing, phone, on-call), escalation paths, SLA targets, and whether support includes integration help or only the platform itself. If a vendor relies on partners, ask who will be accountable when something breaks at 2:00 a.m.
Pricing and lock-in, what vendor proposals often hide
Two proposals can look similar and behave very differently once you scale. The pilot might be cheap because it uses a handful of devices and low retention. Then you add three plants, higher sampling, longer history, and more users, and the bill changes shape.
Hidden cost drivers often include data retention, high-frequency tags, log storage, compute for analytics jobs, and premium support tiers. Also watch for charges tied to connectors or “enterprise” identity features that you assumed were included.
Lock-in is rarely one big trap. It’s usually a pile of small dependencies: proprietary data models, hard-to-export dashboards, custom rules engines, and closed agent software on edge devices. You can still move fast, but keep your exit door unlocked.
Common pricing models and the usage metrics that drive cost
Industrial iot platform vendors typically price around a few common meters. The tricky part is predicting which meter will spike.
| Pricing metric | What it measures | What can spike it |
|---|---|---|
| Per device or per gateway | Connected endpoints | Adding sensors, contractor installs, test benches |
| Per asset | Modeled equipment (pumps, lines) | Better modeling (which is good), wider rollouts |
| Per user | Named or active users | Adding operators, engineers, contractors |
| Message count or data volume | Telemetry throughput | Higher sample rates, more tags, retries after outages |
| Compute | Processing, analytics, AI jobs | More rules, heavier transforms, frequent model runs |
| Storage and retention | Data kept over time | Long history, high-frequency data, extra logs |
When you request a quote, ask for the rate card, overage rules, retention pricing, and what’s included for logs and monitoring. Also ask how support tiers change response times and whether upgrades affect pricing mid-contract.
Ways to reduce lock-in while still moving fast
You don’t avoid lock-in by refusing to build anything. You avoid it by choosing where to standardize.
Start with open protocols (OPC UA, MQTT) and clear data ownership terms. Make sure you can export raw and normalized data in formats your team can use later. Ask for export tools and test them during the pilot, not at renewal time.
Consider splitting responsibilities when it helps. Some teams keep visualization separate from storage, or run key logic at the edge so operations still has visibility during outages. If you use wireless sensors in certain areas, confirm you can integrate common field protocols into your architecture without custom one-offs; this Zigbee mesh networks guide is a useful reference for discussing low-power connectivity choices.
Contract details matter. Ask for an exit clause, define data return formats and timing, and clarify IP terms for custom dashboards, rules, and models. If a vendor builds something “for free” during the pilot, get in writing who owns it.
A simple shortlist process to pick the right vendor
A good selection process keeps arguments factual. It also prevents a quiet mismatch, where IT signs for security and cost, then operations finds the tool hard to use.
Keep it simple:
Define must-haves tied to use cases, score vendors on a short rubric, run a two-week proof of value, then plan rollout in phases. If the vendor pushes for a long pilot, ask what will be different in month three that can’t be proven in week two.
A scoring rubric can be lightweight. Use a 1 to 5 scale across OT fit, integration effort, security readiness, total cost clarity, usability, and support. The goal isn’t math perfection, it’s shared visibility.
The 2-week proof-of-value plan with clear success metrics
A tight proof of value should feel like a sprint, not a research project.
Day 1 to 2: connect real equipment data (one line or one cell). Confirm you can read tags reliably, and confirm timestamps are correct.
Day 3 to 5: normalize and tag data. Map key tags to assets, fix units, add context (site, line, machine).
Week 2: build two to three dashboards and a small set of alerts tied to a real response process (who gets the alert, what they do, how it’s tracked).
Define measurable outcomes before you start. Good ones include time to connect, data quality (missing points, time drift), alert accuracy (false positives), user adoption (do techs actually open it), and security sign-off from IT and OT. If a vendor can’t hit these with one line, scaling to ten lines won’t fix it.
Decision checklist you can share with IT and operations
Bring both groups a single page they can sign.
- OT fit: Works with our PLC and SCADA setup, supports required sampling rates, handles outages with buffering, doesn’t require unsafe network changes.
- IT fit: Clear API strategy, supports SSO, integrates with monitoring and ticketing, predictable admin model.
- Security: Least privilege roles, encryption, audit logs, patch process, documented vulnerability response, supports OT network limits.
- Cost: Quote shows rate card, overage rules, retention costs, support tiers, and likely growth drivers.
- Usability: Operators and maintenance can build and understand dashboards and alerts, training plan is realistic.
- Vendor support: Clear SLAs, escalation path, proven partner help if needed, references in similar environments.
Document assumptions (sampling rate, retention, number of sites) right on the checklist. That prevents surprise costs and “we thought you meant…” debates later.
Conclusion
Choosing among industrial iot platform vendors gets easier when you stop chasing feature lists and start validating real use cases and integration reality. The platform that wins is usually the one that connects quickly, cleans data reliably, passes security review, and stays predictable in cost as you scale. Build a shortlist, request a quote with transparent usage metrics, then run a two-week proof of value using real machine data. What will your first pilot line be, and what metric will prove it worked?